CodePipeline EC2 Action: Simplify your EC2 application deployment pipeline by 90%!
Amazon Web Services (AWS) CodePipeline Team has simplified Developer, DevOps engineers operational overhead and streamlined the Deployment process to EC2 by introducing an CodePipeline action to deploy directly to your EC2 instances.
Why does it matter to you?
Previously, if you wanted to deploy to EC2 instances, you had to use CodeDeploy with an AppSpec file to configure the deployment. After this update NO NEED TO MANAGE CODEDEPLOY RESOURCE AND APPSPEC FILE.
I tried this out today so let me show you how you can simplify your deployment pipeline by 90% and remove all the complex process and scripts!!!
Architecture
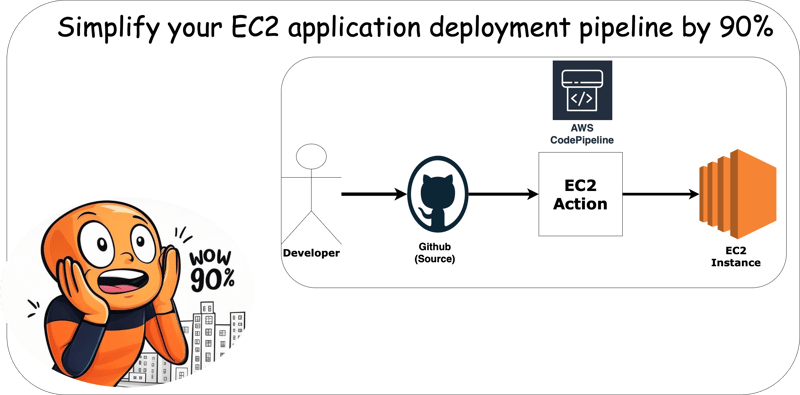
Prerequisites
- supports only Linux instance types
- maximum fleet size supported is 500 instances.
- Pipeline V2 only supported
- SSM Agent must be installed
Behind the Scenes
This action performs a send-command using SSM to execute the script in the instance.
Create an EC2 instance with Apache
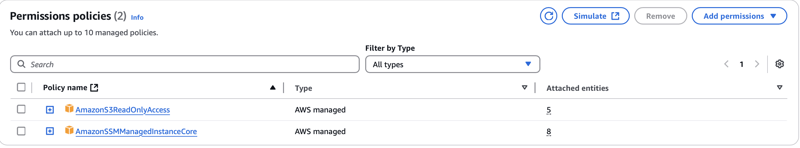
Note: If you are creating an instance then you need to create a role with AmazonSSMManagedInstanceCore, AmazonS3ReadOnlyAccess and attach to ec2 instance.
- Add ssm agent to the instance manually either using
user dataor logging into existing instance and then running the commands. - If you are using existing instance then you need to reboot the instance after adding the ssm agent.
I have created EC2 with Apache web server for the brevity of the blog.
sudo su
yum update -y
yum install httpd -y
service httpd start
chkconfig httpd on
echo "codepipeline ec2 deployment action" > /var/www/html/index.html
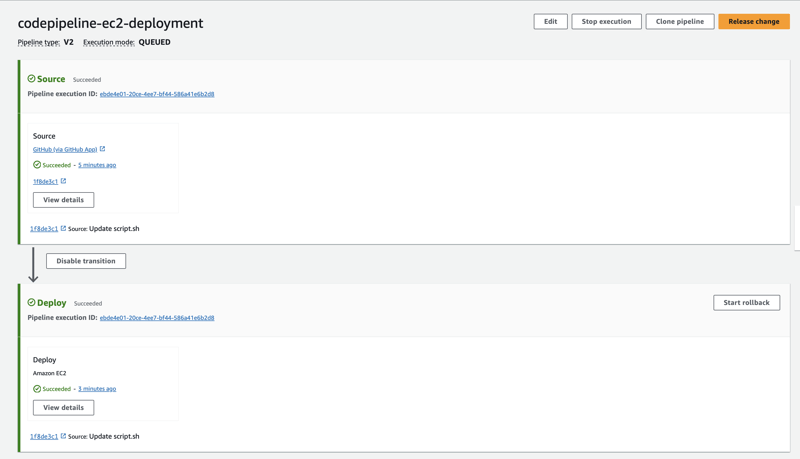
Create pipeline with Ec2 deployment action
- Here we need to select instance using tags; I have used name tag to identify my instance.
- Then you need to provide the target directory in ec2 instance where you want to deploy.
- Finally path to the executable script file that runs AFTER the Deploy phase.
Note: Once pipeline is created you need to edit the pipeline service role and add the following permissions to avoid error.
{
"Effect": "Allow",
"Action": [
"ssm:CancelCommand",
"ssm:DescribeInstanceInformation",
"ssm:ListCommandInvocations",
"ssm:SendCommand"
],
"Resource": "*"
}
Run the pipeline
I am using the source as GitHub using code start connection and code resides in this repo.
Note: The aws guide mentioned about adding AWSSystemsManagerDefaultEC2InstanceManagementRoleeployAction to the ec2 instance role but in my environment I didn’t needed that permission
Some advanced options for this action
- You can specify number of instances in number or percentages to deploy to in parallel.
- You can specify number of instances in number or percentages to stop the task after the task fails.
- You can specify load balancer which will block the traffic Toi the instance when deployment is taking for that instance.
From Developer, DevOps perspective
- With this update I can have an END-to-END AWS native Continuous deployment on EC2 without managing CodeDeploy resources.
- This is surely a game changer for developers and devops engineers who wants to focus on business problem, their applications and not on their complex deployment process.
- Of course this experience of simplifying can be augmented even further to 100% if AWS can add necessary permissions for the role.
After reading this, do you wish to migrate to this action and simplifying your deployment process?
I share such amazing AWS updates on DevOps, Kubernetes and GenAI daily over Linkedin, X. Follow me over there so that I can make your life more easy.

